
9 ways to use ChatGPT as a CSR & Sustainability Leader
ChatGPT is a cutting-edge AI language model that can help CSR and Sustainability managers improve their work in various ways. Here are 9 areas with example prompts how it can…
We are the all-in-one employee engagement platform that lets employees team up to start and join initiatives that they care about and make their business more sustainable, socially responsible, fair & inclusive.








Employees work together and innovate to reduce the environmental impact of their company’s operations.
Employees identify and address social issues that are important to them and align with their company’s values.
Employees can work together to create a culture that values diversity, equity, inclusion and belonging (DEIB).
Activities that are designed to promote the physical, mental, and emotional health of employees in the workplace.
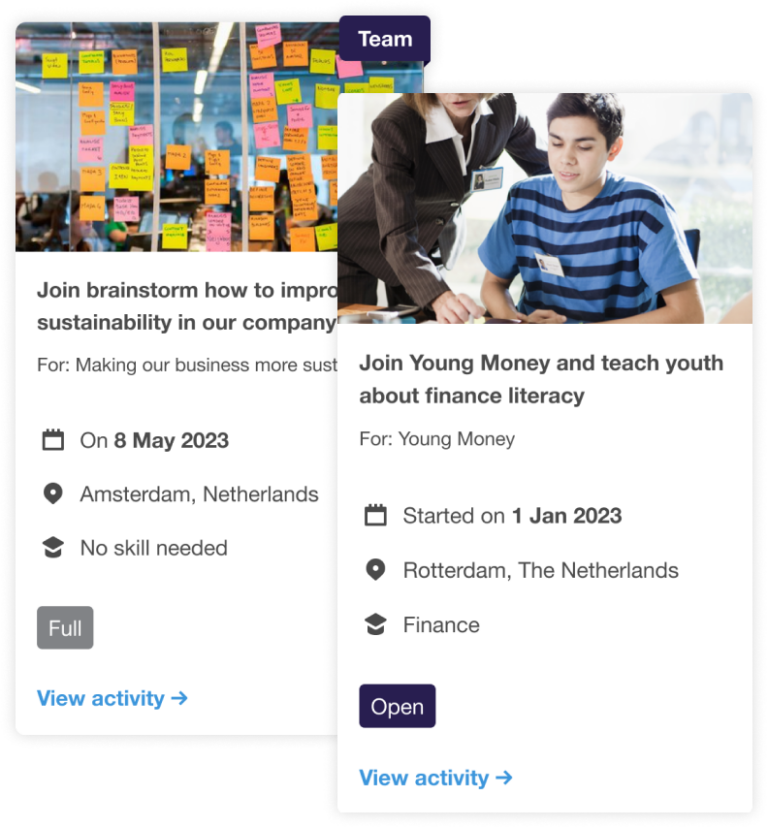
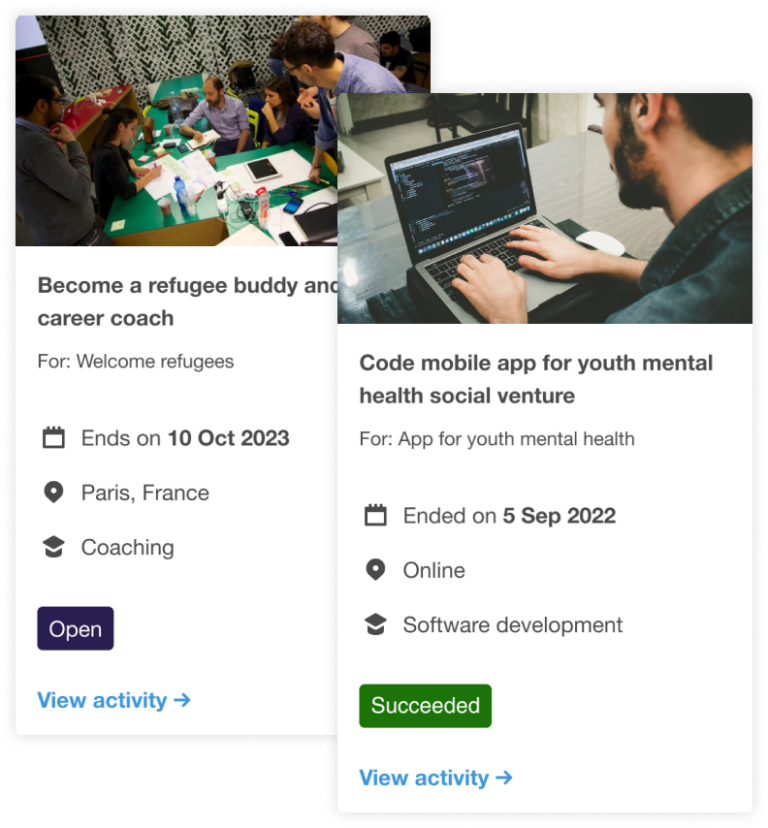
1 – Organise your impact programs effortlessly
Our platform helps you to manage your programs with less time.
2 – Drive meaningful employee engagement
Nudge your employees with gamification towards more engagement.
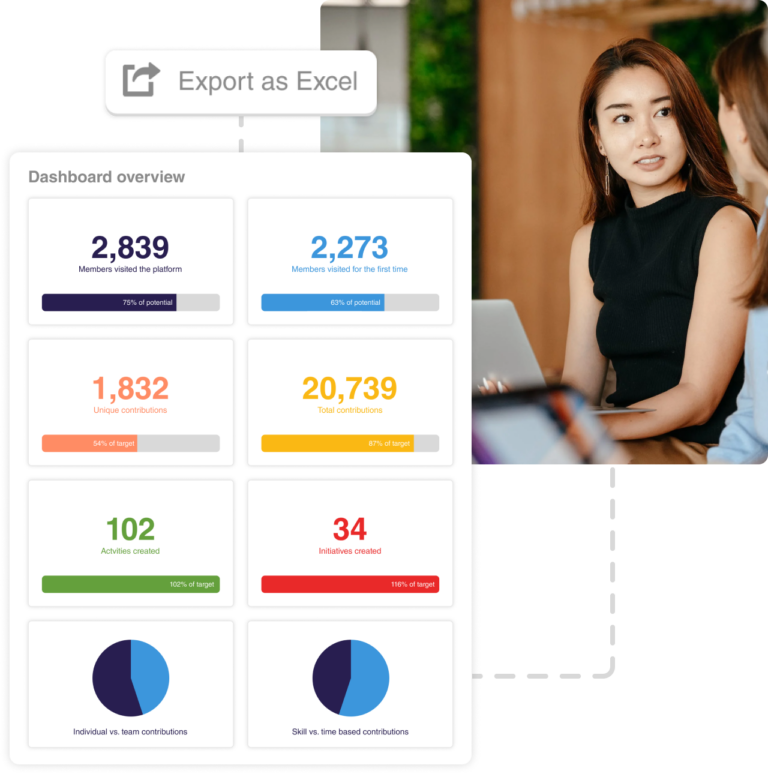
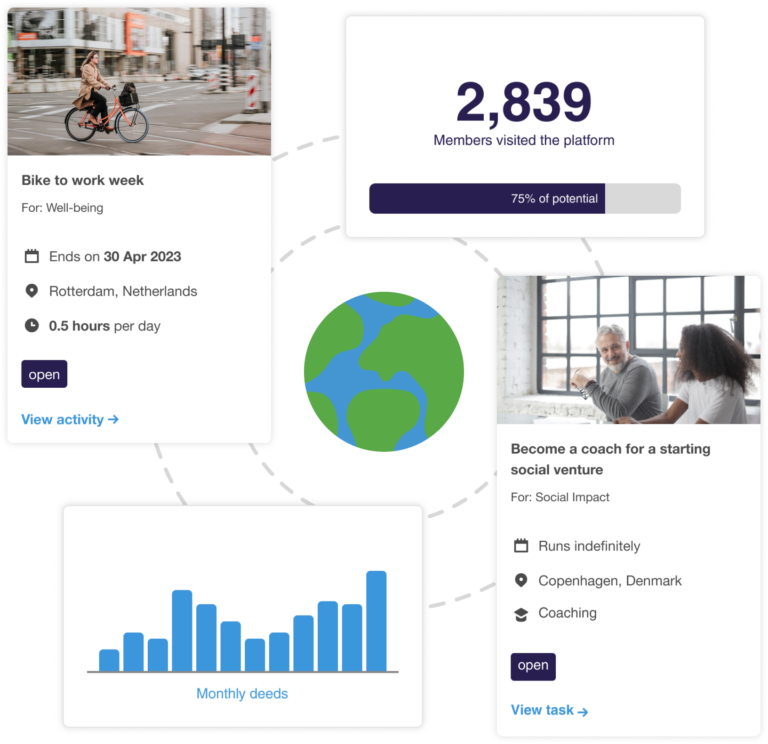
3 – Track & report on engagement & impact
Track and visualise your success across common SDG frameworks.
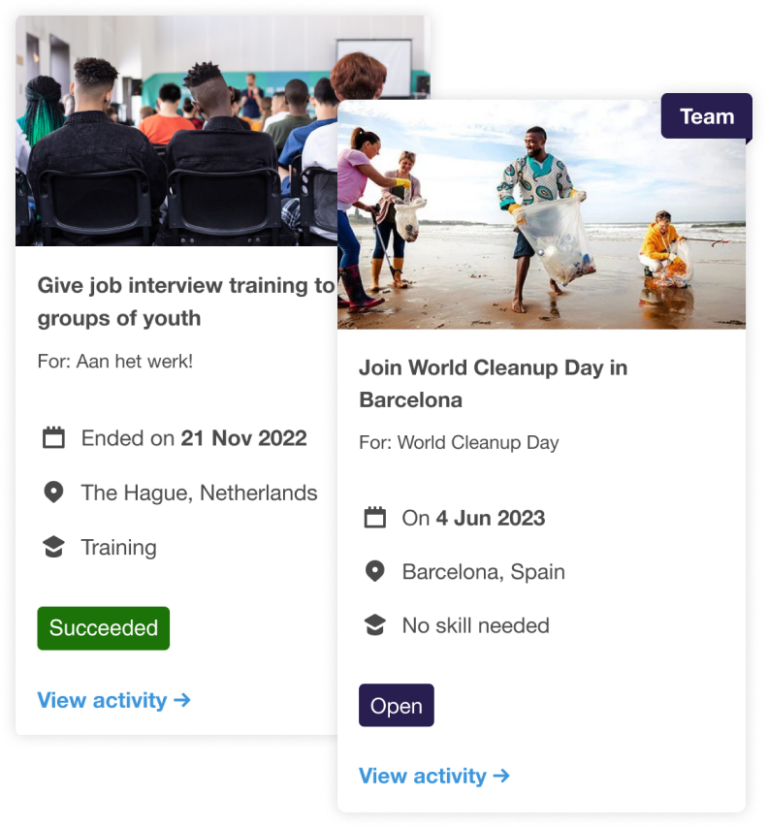
Allows employees to participate in events and volunteering opportunities, either as a group or individually.
Let employees organise and participate in challenges or deeds that promote new behavioural habits.
Invite employees to give back to their communities or support causes that are important to them.
Track and report on the impact of the employee engagement and impact created.
– Laura van den Hurk, Corporate Social and Environmental Responsibility Manager at Accenture


Engaged employees are more likely to stay with a company for the long term, which can help to reduce turnover. Engaged employees are also more likely to attract other top talent.

Employee engagement activities can help to build a sense of community and belonging within your organisation, which can improve morale and foster a positive work environment.

A strong brand reputation that is trusted by both employees and customers can drive business growth, improve customer loyalty, and foster a positive work environment.
We would love to give you a quick demo of our platform and:

ChatGPT is a cutting-edge AI language model that can help CSR and Sustainability managers improve their work in various ways. Here are 9 areas with example prompts how it can…

1 – Let your employees take the lead Empower your employees to play an active role in shaping and implementing your sustainability and impact initiatives. Instead of relying solely on…

The Corporate Sustainability Reporting Directive (CSRD) is an upcoming EU regulation that aims to establish common rules for sustainability reporting by companies. The CSRD builds on the existing Non-Financial Reporting…